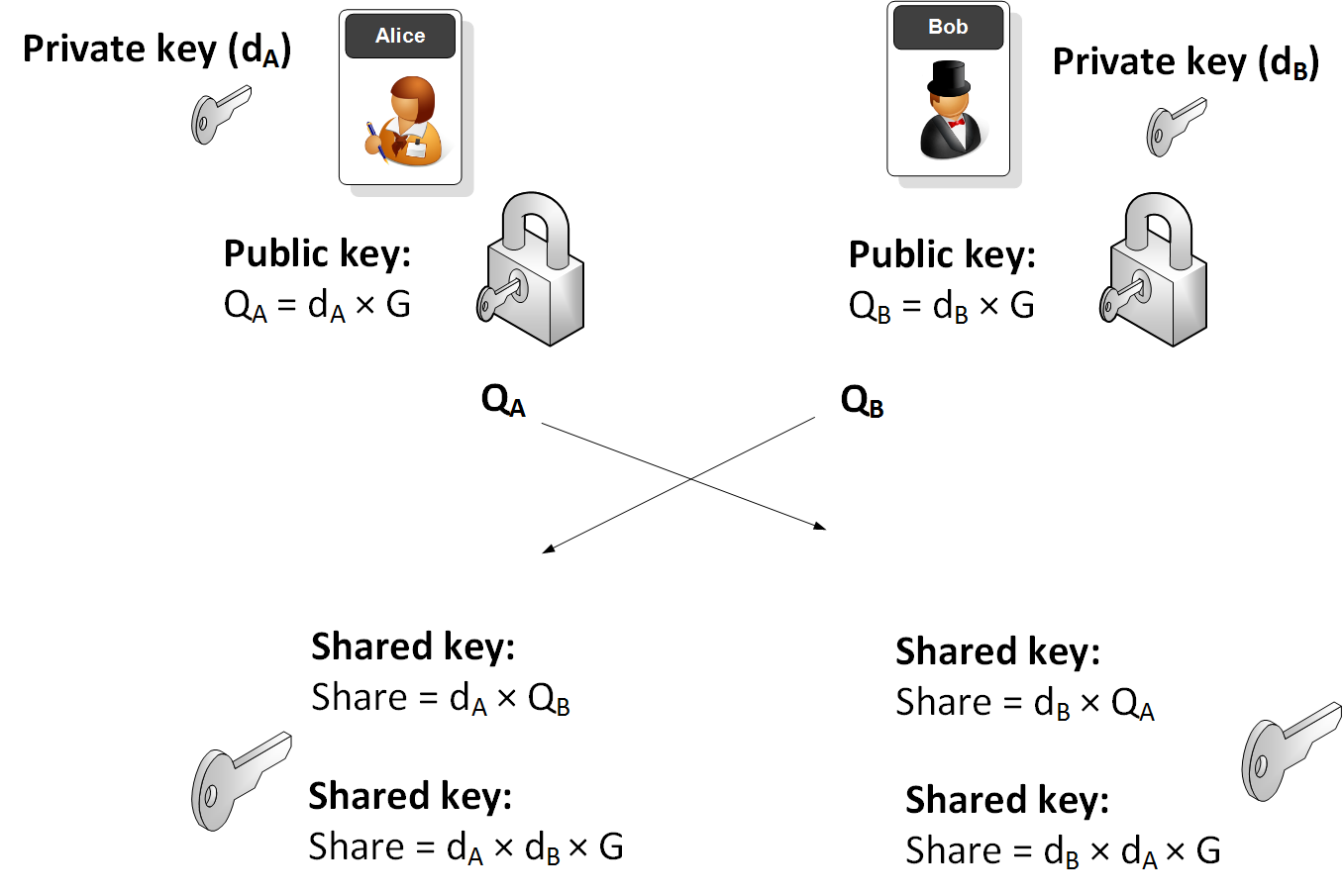
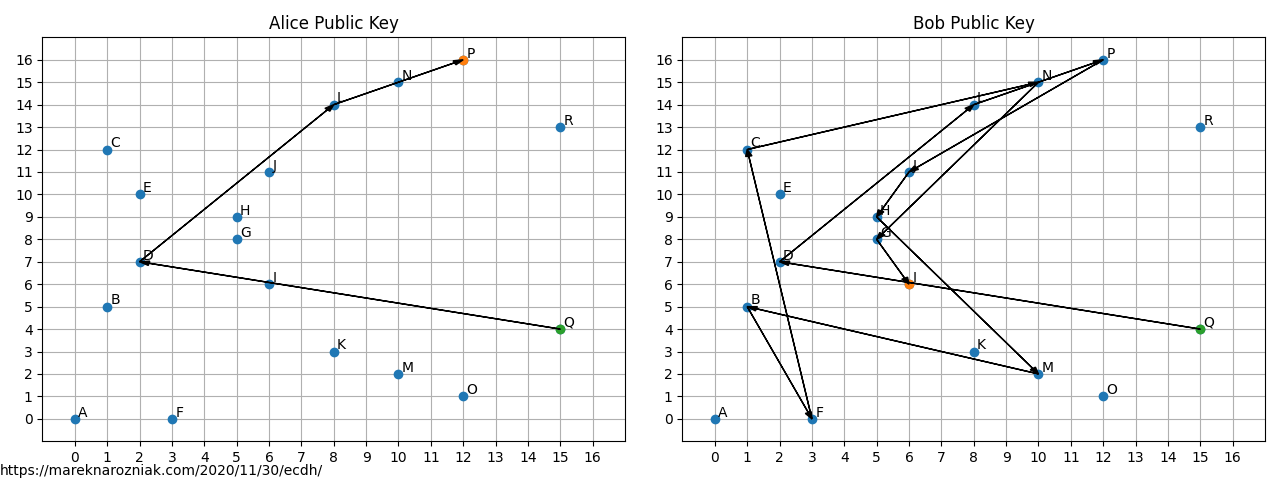
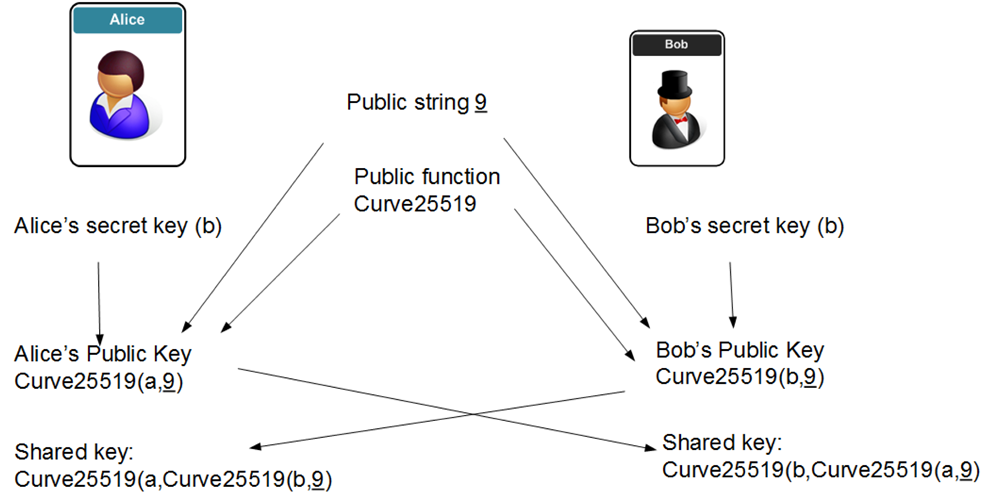
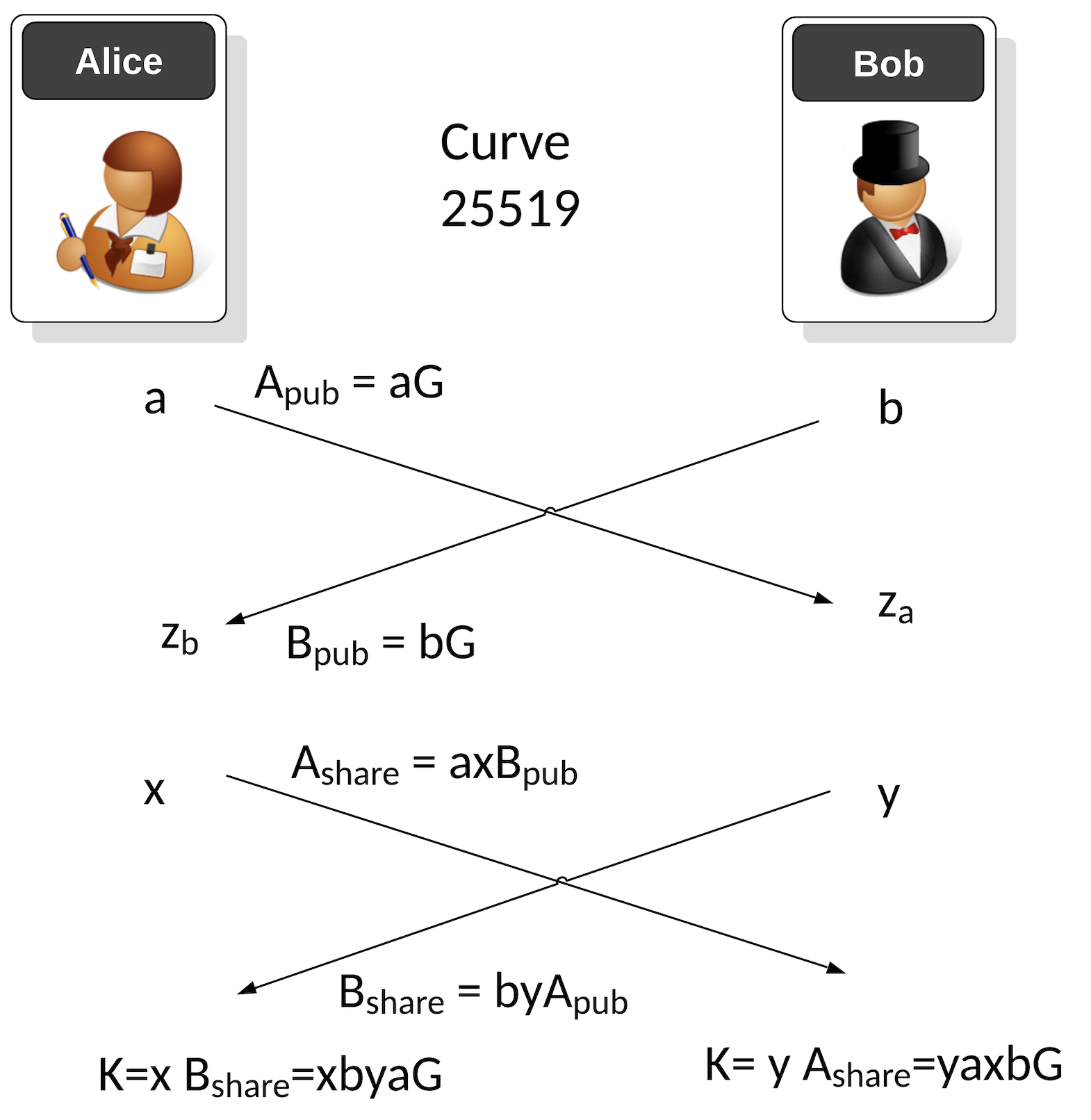
Figure 1 from Performance analysis of point multiplication algorithms in ECDH for an end-to-end VoIP network | Semantic Scholar
GitHub - jeswinMathai/SC-ECDH: Secure Communication System using Elleptic Curve Diffie Hellman Algorithm
GitHub - elesiuta/ECDH: Elliptic-curve Diffie–Hellman key exchange in the binary finite field (GF(2^n))